With hacking strategies and cybersecurity threats evolving on a regular basis, significantly with the quick progress of AI in latest months, e mail safety has turn out to be a essential side of security at work and at house.
Hackers can use your e mail each for the content material and as a manner into your group to conduct a breach of the bigger community. As soon as in, hackers can slither their manner into many information, from confidential monetary information to private data. Right here you can find useful details about the widespread threats to e mail safety and ten greatest practices for a sturdy e mail safety resolution.
Threats to e mail safety
The next are a number of the commonest threats to e mail safety.
Phishing is an assault that asks you for cash or worthwhile data reminiscent of account logins or passwords. Spear phishing is an assault that makes use of your private data to get worthwhile information by impersonating somebody you understand.
Spoofing is an assault the place false information is offered to look reputable, reminiscent of sending an e mail from an account that seems to be an official banking e mail tackle.
Malware is a pc virus, a sort of software program that may get downloaded to your system, which is designed to disrupt a tool, server, or community and usually causes havoc. Malware is a big risk to e mail safety and could be simply downloaded by way of spam when hackers use it to insert malicious hyperlinks, malware, and trojans. Due to this fact, it is essential to take applicable measures to guard your e mail accounts and the contents of your emails from cyber assaults and on-line safety threats.
A DoS assault, or denial-of-service assault, is when a hacker makes a machine or community useful resource unavailable to customers by disrupting the companies of a number related to a community.
- Rising and evolving cyber assaults
Cyber assaults have gotten more and more subtle as AI evolves and helps hackers to write down extra convincing emails. This is the reason it’s important to develop a sturdy e mail safety resolution.
12 greatest practices for a robust e mail safety resolution
So, with all the above in thoughts, let’s delve into some methods to mitigate the dangers posed by cybersecurity with some easy greatest practices you could apply instantly.
1. Make robust passwords and encryptions
Everyone knows that we should always use robust passwords and keep away from utilizing the identical one twice, however it may be an actual ache. Generally remembering your telephone quantity is difficult, not to mention dozens of passwords. Fortunately, many units can safely retailer your passwords so that you simply don’t need to enter them every time, and a few apps retailer your passwords for you.
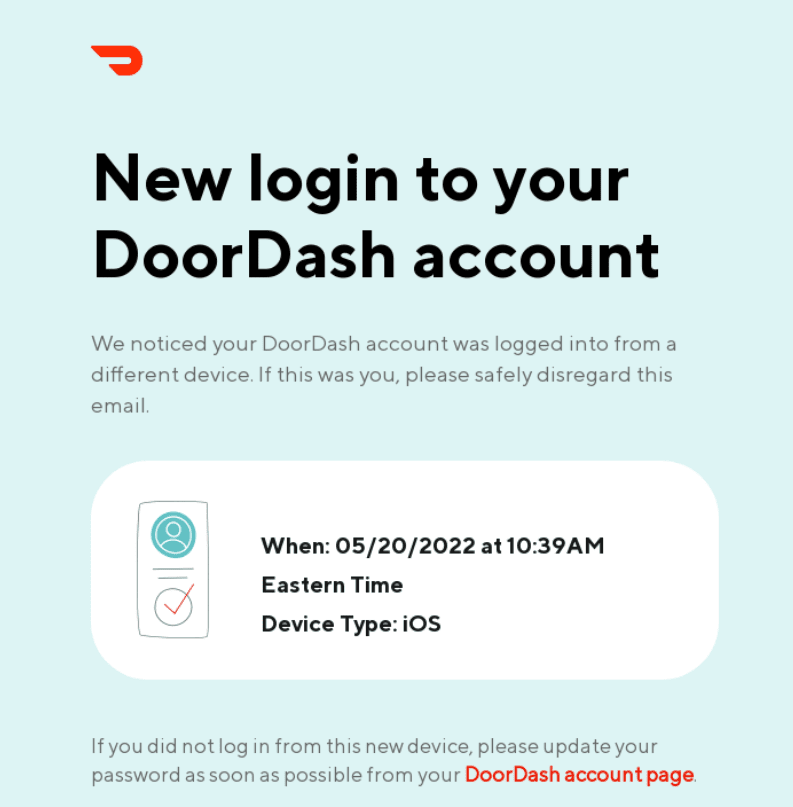
(Supply: Actually Good Emails)
Subsequent, we now have encryption: each time you ship a thank-you e mail (or any e mail for that matter), there may be some threat that will probably be intercepted by a hacker on its journey between you — the sender — and the recipient. So what does encryption do? It scrambles your e mail’s content material so anybody intercepting it may well’t learn it. Solely with authentication from the recipient can the true message be learn. This additionally signifies that in the event you by accident ship an e mail to the unsuitable tackle, the recipient gained’t be capable to learn it.
Many e mail companies, reminiscent of Gmail and Microsoft Outlook, in addition to safe e mail suppliers like Mailfence, supply encryption as a function. Defending your inner audit report instance and different important paperwork turns into a lot simpler with encryption.
2. Again up your vital emails
In addition to defending your information from being seen by undesirable eyes, you additionally wish to defend it from getting misplaced or deleted. This is the reason it’s an ideal concept at all times to again up any vital emails. You may go for an exterior arduous drive or a USB stick or add information to the cloud.
There are advantages and downsides to all of those. A bodily exterior arduous drive or USB stick can get misplaced or broken, and there have been situations prior to now of hackers stepping into cloud storage options and stealing information that manner.
There isn’t any good resolution, however safety for cloud storage has improved over time. Having a bodily copy of your vital information will help in case your system decides to exit the land of the residing.
3. Educate everybody about suspicious emails and hyperlinks
Whereas numerous cybersecurity comes right down to tech, quantity of it’s about widespread sense and instructing greatest practices, reminiscent of acknowledge and take care of suspicious-looking emails or use e mail monitoring software program. You may run easy webinars, use video tutorials to simplify the method and add a quiz to make sure everybody has reached a selected customary throughout the group.
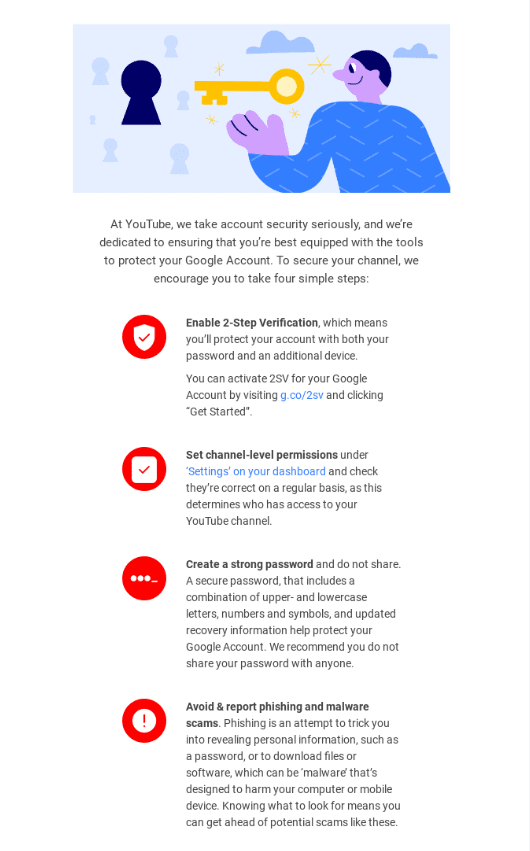
(Supply: Electronic mail from YouTube)
Annual refreshers with up to date data would additionally assist the method, and you’ll try the SOC 2 certification price if you wish to go the additional mile with coaching your workers in all issues audit-related.
4. Hold your accessibility confidential
Proxies assist you to preserve your location data personal, ship emails and conduct on-line analysis with out worrying about Google third-party cookies monitoring you. Particularly for emails, proxies assist you to ship them with out exposing your IP tackle.
So how does it work? Proxy servers act as a gateway between you and the web, separating you and different customers from the web sites you browse. Web visitors goes by way of the proxy server to the tackle you typed in. The request comes again by way of that very same proxy server, and you might be forwarded the information acquired from the web site.
5. Set up up-to-date antivirus safety
You may’t simply ignore your antivirus and depart it within the nook. It wants consideration generally, so don’t ignore these pop-ups telling you that it’s good to obtain the most recent model of the app. An previous model will rapidly turn out to be out of date towards the fixed tide of hacking, so guarantee your defenses are fortified with the most recent updates and dependable e mail safety instruments.

(Supply: Actually Good Emails)
6. Enhance your spam filter
You need to use an e mail content material filter to intercept incoming messages and examine them for malware or different harmful components. After this course of, your “How safe is RDP?” e mail will get delivered to its vacation spot or quarantined so that you can assessment if mandatory.
Screening incoming communications earlier than they attain you or your group can defend you massively. This course of lets you take a look at messages with out opening them and block spam messages and malware earlier than they’ll attain your colleagues’ inboxes.
One other efficient manner to enhance e mail safety is to make use of e mail verification instruments. These instruments will help be sure that solely reputable emails are delivered to your inbox whereas blocking spam and phishing makes an attempt.
With so many choices in the marketplace, realizing which instruments are the perfect on your wants could be troublesome. To make the choice course of simpler, it is value testing a number of the greatest e mail verification instruments out there and discovering one which fits your group’s necessities.
7. Make your e mail advertising and marketing contact checklist safe
That is essential for sustaining your prospects and audiences’ belief. In spite of everything, digital safety isn’t solely about your information but additionally your prospects’ information. On the subject of e mail, this implies taking good care of your e mail advertising and marketing contact checklist.
To do that, it is best to be sure to restrict who has entry to your e mail advertising and marketing checklist and retailer it securely in restricted locations (e.g., in a safe database). It’s because the extra those who have entry and the extra copies that exist, the extra doubtless it’s that the checklist can be compromised.
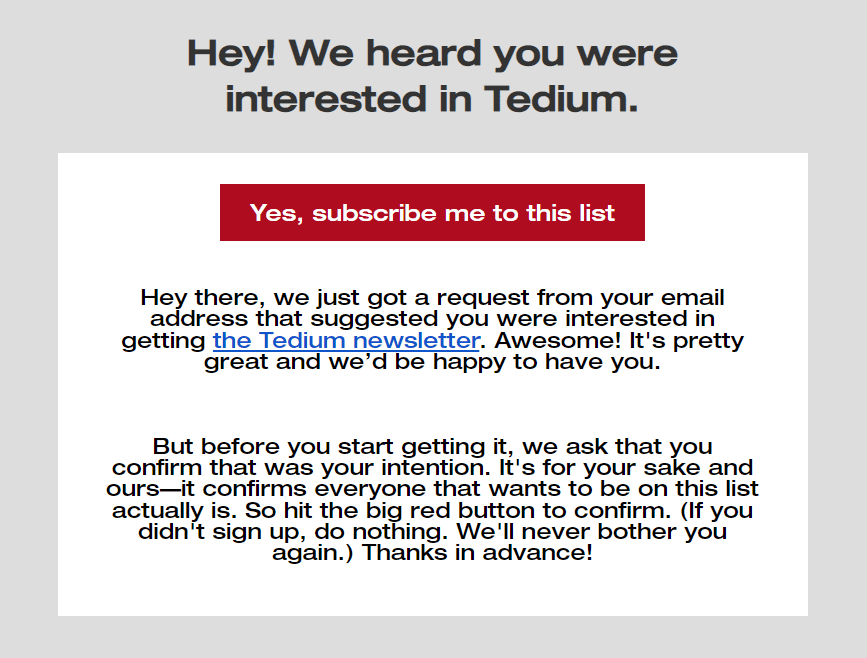
(Supply: Electronic mail from Tedium)
You possibly can additionally think about organising a double opt-in sign-up course of, which creates a further step for patrons to subscribe to a mailing checklist. This can scale back the probability that your advertising and marketing emails are being despatched to bots or invalid e mail addresses, in addition to guarantee your prospects that they gained’t be receiving emails they don’t need.
8. Allow SPF, DKIM, and DMARC authentication
There are three kinds of e mail authentication you could configure: Sender Coverage Framework (SPF), Domainkeys Recognized Mail (DKIM), and Area-based Message Authentication, Reporting & Conformance (DMARC). Collectively they assist mailbox suppliers and spam filters to acknowledge that your e mail is reputable and could be trusted.
This fulfills two aims. Firstly, they’re important configurations that defend your model’s repute. It’s because they scale back the probability of an unauthorized person sending emails below your area with out your consent or information.
On prime of this, in addition they be sure that the emails you ship attain their desired recipient. Lowering the danger that they find yourself in a buyer’s or shopper’s spam folder or are flagged as a risk.
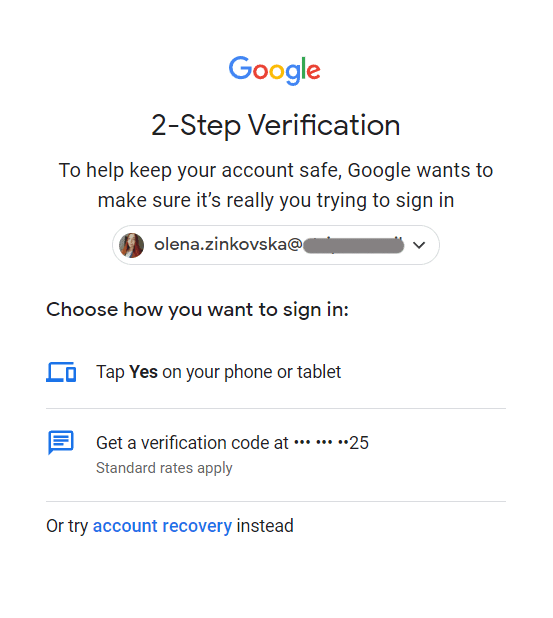
9. Allow two-factor authentication
Two-factor and multifactor authentication are nice choices that massively improve your e mail safety.
That is the way it works: once you log in to your e mail, you enter your password, which triggers a code despatched to your smartphone for verification. With out this code, you may’t entry your account, so even when a hacker have been to get their palms in your password, your data would stay secure.
10. Replace your OS
Commonly updating your working system is important for e mail safety since updates can add new options. Updates additionally repair or patch any vulnerabilities within the system. Patches take away bugs and gaps that hackers may use to achieve entry to your laptop and information.
11. Solely belief dependable sources
In the event you obtain an e mail with a hyperlink to click on on, at all times examine the place that hyperlink goes to direct you earlier than clicking on it. You may sort the web site tackle into your browser to make sure that it is not going to redirect you to a pretend website.
If it seems to be suspicious for any purpose, do not click on on it, even when it seems to have been despatched from somebody you understand. As a substitute, it is best to contact the particular person and ask in the event that they despatched you the e-mail.
Studying the tell-tell indicators of a phishing e mail may prevent numerous stress and fear and is essential in e mail administration. The next are indicators that an e mail is a rip-off, even when it seems to be prefer it comes from an organization you belief and even makes use of its emblem:
- a generic greeting or the primary half of the e-mail as an alternative of your title. the drill: “Hi there ant_man_fan78..”;
- the e-mail claims that your account is on maintain due to a billing downside;
- the e-mail asks you to click on on a hyperlink to replace your cost particulars.
Actual corporations won’t ever e mail or textual content with a hyperlink to replace your cost data. It’s additionally extraordinarily uncommon for reputable corporations to ship emails with typos, which is one other widespread signal of phishing emails. Nonetheless, AI is making it simpler for hackers to enhance the grammar of phishing emails.
12. Implement worker compliance
Lastly, all of this data is ineffective except utilized, so be sure that your colleagues and staff (and employers!) are taking heed of e mail safety protocols and making use of them as mandatory.
To remain forward of the curve, be certain that to frequently assessment and replace your e mail lists and spend money on respected checklist administration instruments. Maintaining with the most recent developments in e mail safety will help defend what you are promoting from potential cyber-attacks. Overview The Electronic mail Record Decay Report for 2023 for extra insights.
Wrapping up
Preserving your emails secure isn’t rocket science, however it requires some forethought and consideration, particularly in the event you’re operating a enterprise of any dimension. Nobody is secure from hacking or trying like a pretty goal.
This is the reason it’s good to defend your e mail and information and again every thing up. Whether or not you’re an e mail marketer or an accountant at your organization, in the event you work with emails (and nearly all of us do), it’s good to know what’s up with safety.
Be part of Stripo to save lots of time and construct skilled emails stress-free