On a regular basis APIs are working behind the scenes to offer a satisfying digital expertise to each person.
The flight journey you got on-line, a recipe you shared on Fb, and an affordable film ticket you booked are all due to APIs.
API safety helps flawlessly ship built-in person expertise from one machine to a different presenting a treasure of enterprise alternatives.
An Utility Programming Interface (API), is a software-to-software interface. Functions are supplied with a safe and standardized path by APIs to work with one another and ship data or performance requested with out guide intervention.
As expectations for easy person expertise enhance, corporations are APIs to ship additional worth to customers in a jiffy. By leveraging APIs to entry sure information, piece of code, software program, or companies, you possibly can improve the performance of your product plus save money and time.
If the appliance offering the useful resource can present what the shopper needs, then the API will return what is required or a standing code which implies performed. If the server isn’t in a position to full the request, then the API will return an error message.
Implementing new APIs for an internet utility is a superb expertise. Third get together builders’ profit whereas integrating with one other app. Shoppers additionally profit from an app’s integration, and it’s worthwhile as extra customers get drawn to the platform.
However hackers too are preserving watch for brand spanking new APIs because it is a chance for them to take advantage of the data saved on servers.
What Is API Safety?
API safety is a fashion of defending APIs from abuse or cyber-attacks. API safety ensures all requests which might be processed by the API are respectable, legitimate, and responses from the API are protected against interference or exploitation.
APIs goal to facilitate (usually personal) switch of knowledge, between a system and an exterior person. Due to this fact, a poorly maintained and insecure API could cause lack of delicate information.
We now have heard again and again about billions of information being uncovered attributable to cyber-attacks and insecure APIs.
API hacks have affected companies similar to FB, Venmo, Twitter and USPS. To remain secure and defend delicate information, combine API safety rules.
Why Is API Safety Vital
Cyber safety covers all on-line applied sciences, however APIs are positioned between third-party builders and a useful resource. API safety breakdowns are detrimental to each the appliance and its customers. It is because the hacked endpoint offers entry to delicate information.
A hack-attack could cause monetary loss and hurt your model picture. Prospects lose their belief and corporations their credibility whereas utilizing an insecure API. Third-party built-in apps can also get affected by way of an extension.
REST API safety vs SOAP API safety
Net API safety takes care of the switch of knowledge via APIs which might be linked to the web. OAuth (Open Authorization) is an open commonplace to delegate entry. What it does is permits customers to offer third-party entry to net sources.
That is with out having to share passwords. OAuth is the expertise commonplace that permits sharing of allows you to share any video to your social networks via a one contact share button.
Most API implementations are of two varieties: REST (Representational State Switch) or SOAP (Easy Object Entry Protocol).
REST API makes use of HTTP in addition to assist (TLS) Transport Layer Safety encryption. TLS is a normal that retains an web connection personal and checks information despatched between two methods (server to server, or server to shopper) is encrypted and unmodified.
This implies if a hacker is making an attempt to collect your bank card data from a procuring web site, he can neither learn your information nor modify it. To test if a web site is protected with TLS – the URL begins with “HTTPS” (Hyper Textual content Switch Protocol Safe).
REST APIs additionally use JSON, this file format that makes it simple to switch information over net browsers. By utilizing a mix of HTTP and JSON, REST APIs don’t need to retailer or repackage information. Therefore it makes them quicker than SOAP APIs.
SOAP APIs use built-in protocols known as as Net Providers Safety (WS Safety). These protocols outline a algorithm guided by privateness and authentication. They use XML encryption, XML signatures, and SAML tokens to confirm verification and sanction.
Basically, SOAP APIs are praised for having extra complete safety measures, however they want increased dealing with. Due to this fact, SOAP APIs are endorsed for corporations dealing with delicate information.
Sorts of API Cyberattacks
Widespread assaults in opposition to APIs
Stolen Authentication
The best option to entry an API is to swindle it utilizing the identification of a licensed person. As soon as the authentication token will get into unsuitable palms, entry to sources are compromised and knowledge is retrieved by showing respectable however with depraved intent.
Cybercriminals additionally generally attempt to guess authentication passwords. Or they could even break a frail authentication course of to realize entry.
Man-in-the-Center Assault
A person-in-the-middle (MITM) assault is referred to the incidence whereby a hacker intercepts an API request or the response going down in between an end-user and an API.
Delicate contents could also be stolen throughout this communication like login credentials, fee data or the contents of the request/response could possibly be modified.
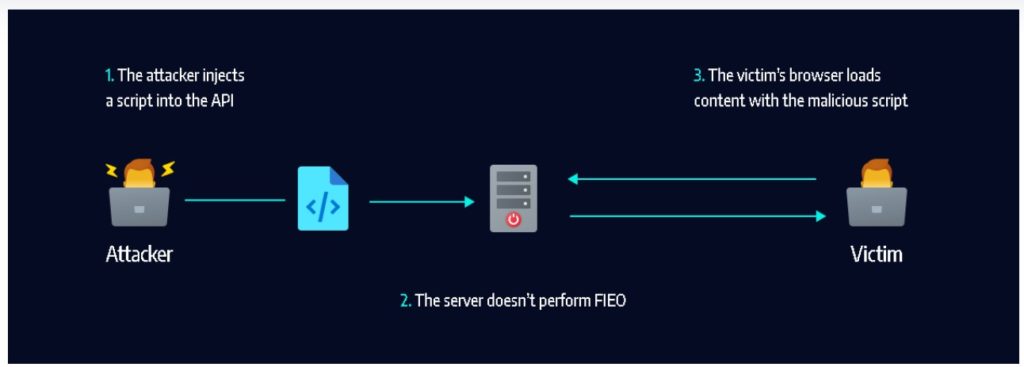
Code Injections
APIs with breaches in authentication and validation are weak to code injections. Right here often an attacker sends a script to the appliance’s server utilizing an API request. This script can expose or delete information, place false data, and hurt an app’s internals.
Generally the time period “SQL injection” perhaps used. Code injection usually happens on a SQL database.
Denial-of-Service Assault
A distributed denial-of-service assault is a cyber-attack that endeavours to sluggish or crash a web site / net server / net service with API requests. That is performed by overloading its server or community sources with net site visitors.
A distributed denial-of-service (DDoS) assault is commonly occasions made concurrently from a number of malicious sources.
However these dangers don’t imply APIs will get redundant. Any on-line utility looking for to combine with a useful resource wants an API. And each new API is a chance for hackers to pilfer private information. Due to this fact each software program integration ought to undertake correct API-specific safety measures.
With an Engineering diploma and a Diploma in Administration underneath my belt, I labored for 16+ years within the vehicle business with numerous producers in numerous capacities. However my ardour for writing was overwhelming, therefore I turned that right into a profession. I’ve been writing for greater than 10+ years on numerous domains together with the IT business. I’m certain one can find the 200+ revealed blogs of mine in right here informative, exhaustive and attention-grabbing.